How to make your own mail server and avoid getting your mail in spam?
You need to send your emails with a proper DKIM, DMARC and SPF signification!
Postfix
- Install all required software:
apt-get install opendkim opendkim-tools postfix-policyd-spf-python postfix-pcre
sudo adduser postfix opendkim
Opendkim
Configure opendkim
- Create a opendkim keys directory:
mkdir -p /etc/opendkim/keys
- Generate a keys:
export DOMAIN=burlutsky.su
cd /etc/opendkim/keys/
mkdir $DOMAIN
cd $DOMAIN
opendkim-genkey -s mail -d $DOMAIN
Here is a mail selector name. Replace burlutsky.su with your domain name.
- Create your signing table:
cat >>/etc/opendkim/SigningTable <<EOF
*@$DOMAIN mail._domainkey.$DOMAIN
cat /etc/opendkim/TrustedHosts
127.0.0.1
localhost
$DOMAIN
*.$DOMAIN
EOF
- Create a key table:
cat > /etc/opendkim/KeyTable <<EOF
mail._domainkey.$DOMAIN $DOMAIN:mail:/etc/opendkim/keys/$DOMAIN/mail.private
- Add your files definition to the
/etc/opendkim.conffile:
AutoRestart Yes
AutoRestartRate 10/1h
SyslogSuccess Yes
LogWhy Yes
Canonicalization relaxed/simple
ExternalIgnoreList refile:/etc/opendkim/TrustedHosts
InternalHosts refile:/etc/opendkim/TrustedHosts
KeyTable refile:/etc/opendkim/KeyTable
SigningTable refile:/etc/opendkim/SigningTable
Mode sv
Socket inet:12301@localhost
- Enable opendkim daemon running on the localhost TCP socket. Change:
/etc/defaults/opendkim
SOCKET="inet:12301@localhost"
- Add new postfix milter with the opendkim socket. Add to
/etc/postfix/main.cf:
milter_protocol = 2
milter_default_action = accept
smtpd_milters = inet:localhost:12301
non_smtpd_milters = inet:localhost:12301
policyd-spf_time_limit = 3600
smtpd_helo_required = yes
smtpd_recipient_restrictions =
permit_mynetworks,
permit_sasl_authenticated,
reject_unauth_destination,
check_policy_service unix:private/policyd-spf
smtp_tls_security_level = may
smtp_tls_ciphers = export
smtp_tls_protocols = !SSLv2, !SSLv3
smtp_tls_loglevel = 1
- Set permissions:
chown -R opendkim:opendkim /etc/opendkim
- Edit /etc/postfix/master.cf and add the following entry at the end:
policyd-spf unix - n n - 0 spawn
user=policyd-spf argv=/usr/bin/policyd-spf
- Enable and start services:
systemctl enable postfix
systemctl restart postfix
systemctl enable opendkim
systemctl restart opendkim
DNS
Now we need to configure DNS system. Add all DNS records below:
- SPF record.
TXT "v=spf1 a:burlutsky.su -all"
replace burlutsky.su with your domain.
- Now you need to get a DKIM key.
cat /etc/opendkim/keys/$DOMAIN/mail.txt
You can see something like this:
mail._domainkey IN TXT ( "v=DKIM1; h=sha256; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAq+...) ; ----- DKIM key mail
Add this text record to the DNS system.
- Turn on DMARC:
_dmarc.burlutsky.su IN TXT "v=DMARC1; p=none; sp=none;"
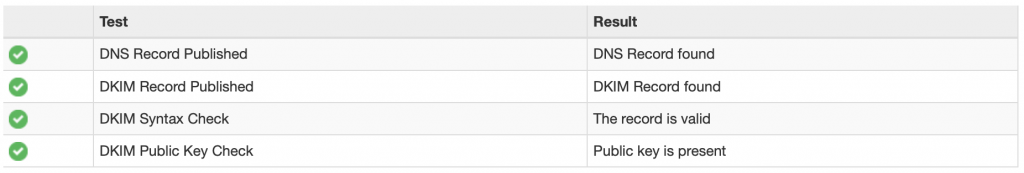
- Test your email with gmail or online services like this: https://mxtoolbox.com/dkim.aspx . Set selector =
mail.